Conclusion
This module will review critical lessons from your security awareness training to increase team retention of core program content.
2:05 minutes
*Courses may vary.
Search Courses
This module will review critical lessons from your security awareness training to increase team retention of core program content.
2:05 minutes

The module will outline cyber threats (established and emerging), recent attacks and industry regulations, and also position employees as key players in modern cybersecurity initiatives.
5:13 minutes



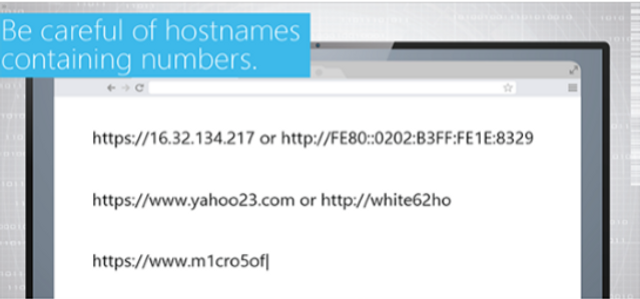
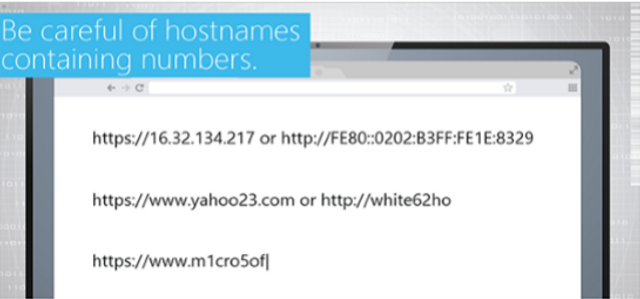





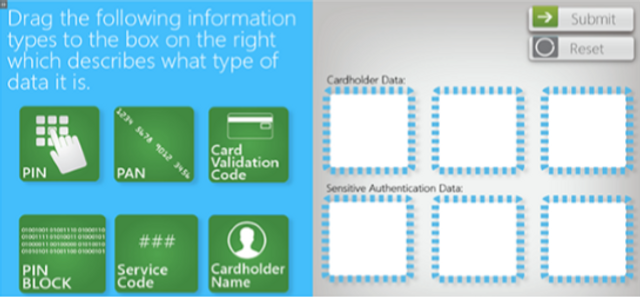
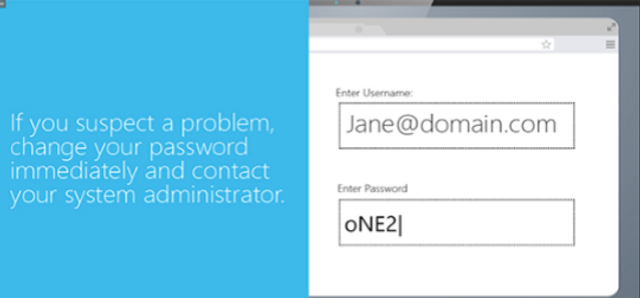
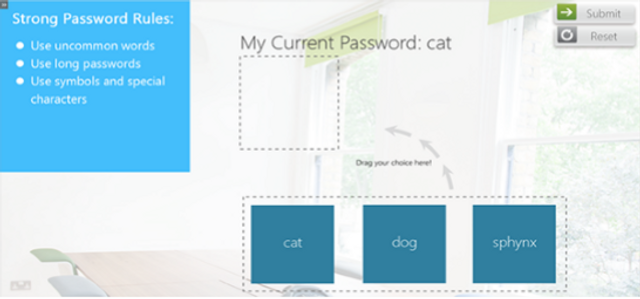

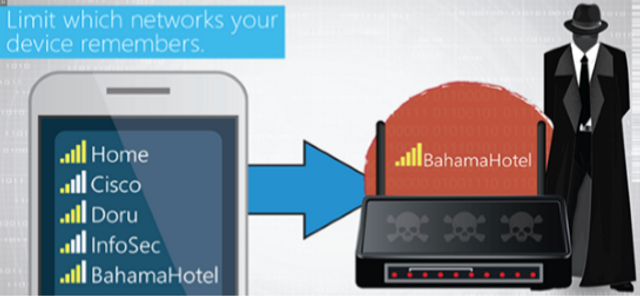
Our Mobile Wi-Fi Security module explains how to safely use wireless devices when operating on Wi-Fi connections.
2:07 minutes
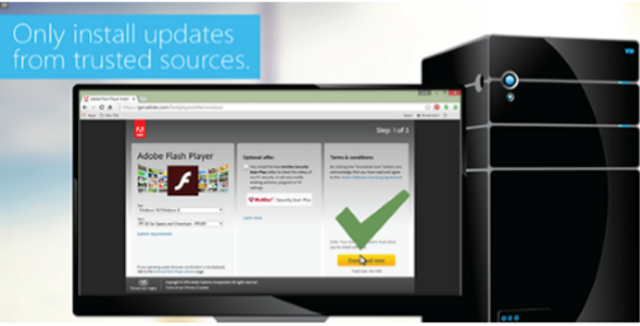
This module focuses on three key ways to prevent malware infections, details common sources of malware infections and discusses methods to help users avoid unsafe files.
3:21 minutes

This interactive module defines malware in common terms, details the dangers it poses to organizations, and discusses preventative actions.
17:01 minutes

In just one minute, this video explains the risks of connecting to public Wi-Fi networks, including how sensitive information can be intercepted by attackers.
1:00 minutes

In less than one minute, this video reinforces the importance of keeping passwords private.
1:00 minutes

Please complete and submit the form below.

