Creating Strong Passwords (Video)
This short video details the process of choosing secure, robust passphrases in under one minute. 0:46 minutes
*Courses may vary.
Search Courses





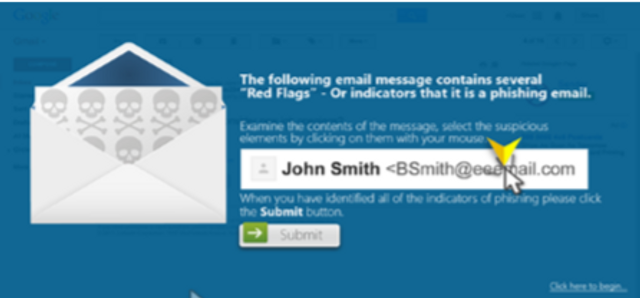


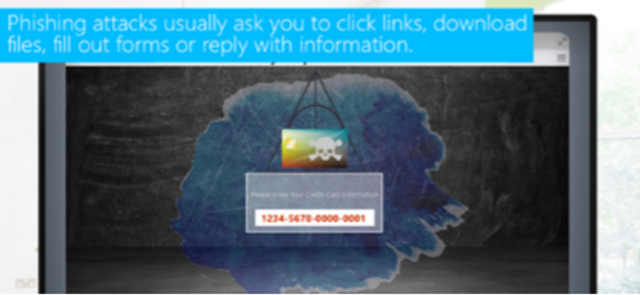



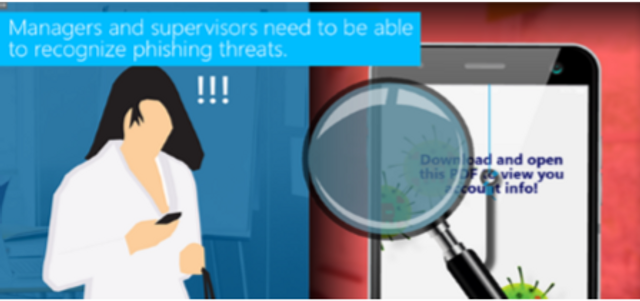










Please complete and submit the form below.

