Phishing Assessment (Capital One) W/ Hints
This assessment module will test a learner’s ability to recognize suspicious email elements through a realistic email mimicking Capital One communications.
0:30 minutes
*Courses may vary.
Search Courses

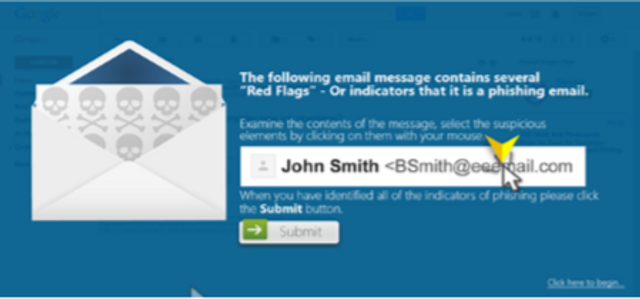
This assessment module will test a learner’s ability to recognize suspicious email elements through a realistic email mimicking Capital One communications.
0:30 minutes


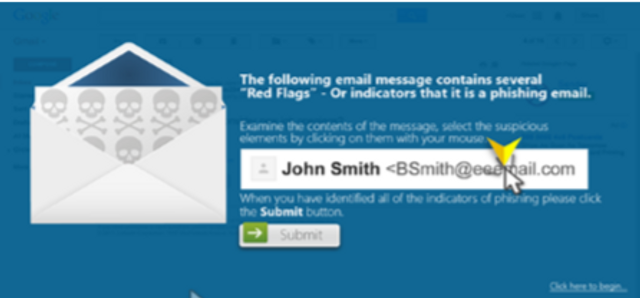
This assessment module will test a learner’s ability to recognize suspicious email elements through a realistic email mimicking Capital One communications.
0:30 minutes
This advanced assessment module will test a learner’s ability to recognize suspicious email elements through a realistic email mimicking LinkedIn communications.
0:30 minutes

This module details best practices for detecting and reporting unauthorized Protected Health Information (PHI) disclosures.
8:14 minutes
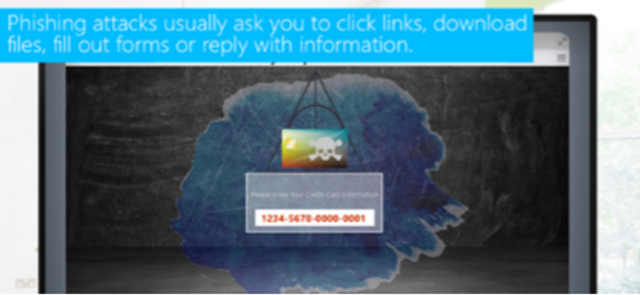
This short video covers some of the common signs of phishing emails and how to recognize malicious links.
2:27 minutes


This module teaches learners how to avoid falling victim to phishing.
2:11 minutes
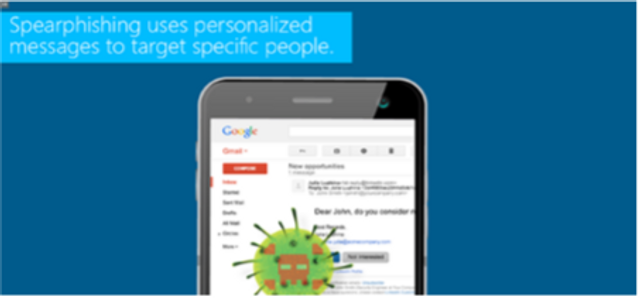
This interactive training explains how financial sector employees and customers are targeted by phishing attacks and teaches users how to recognize phishing attacks.
10:23 minutes


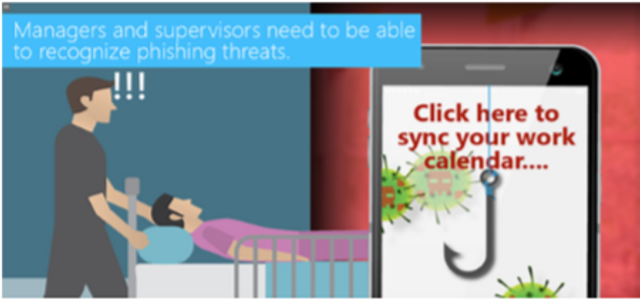


This module explains the risks phishing poses to executives and organizations, and suggests ways executives can work with their security teams and staff to keep information secure.
10:04 minutes
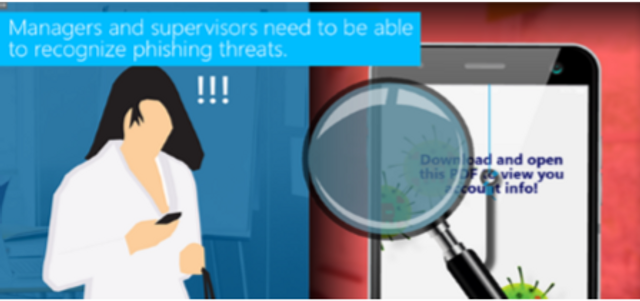
This module discusses phishing in detail and teaches managers how to detect phishing attempts. It also outlines how managers can work with their teams to protect their company from phishing attacks.
11:02

Target sighted! Follow the hunt of that vicious but sometimes misaimed predator, the Spearphish.
1:30 minutes

The wonders of nature are displayed up close as the Whaling Shark chases its prey, the powerful and important Whale.
1:23 minutes

Dive into the Sea of Emails for a closer look at one of the oldest scams still swimming today: the Common Phish.
1:25 minutes

Sink into the depths to observe the Clone Phish, which disguises itself as a previously trustworthy message to lure in prey.
1:18 minutes


This interactive training module covers voice phishing, or vishing, a simple but effective technique cybercriminals and scam artists use to collect confidential information.
6:44 minutes

Spearphishing occurs when phishing messages are tailored for targeted individuals. This interactive module will help teams identify and avoid spearphishing attempts.
2:40 minutes
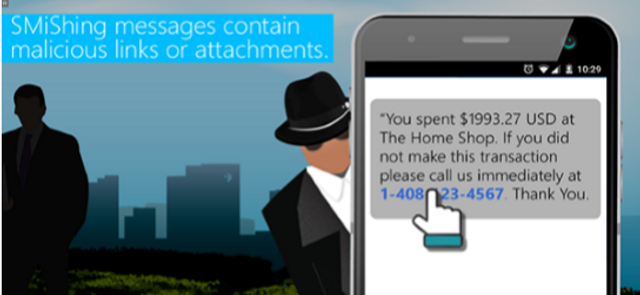
SMS Phishing, or SMiShing, is used by cybercriminals to collect valuable information and distribute malware. This module includes effective ways to stop SMiShing attempts.
4:58 minutes

This module will introduce learners to the concept of phishing, teach them how to quickly identify phishing messages and show them how to verify whether or not a message is legitimate.
2:49 minutes

Please complete and submit the form below.

