Training
Training Courses
Course Catalog
*Courses may vary.
Search Courses

Score! (Encryption)
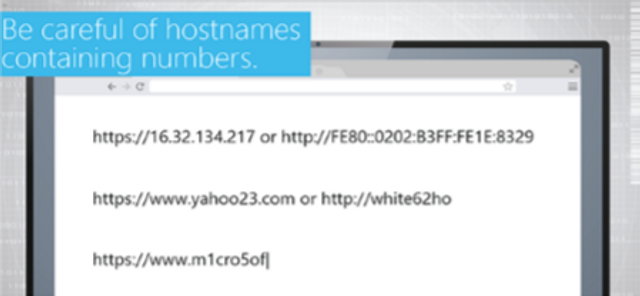
Safe Harbor (Safe Web Browsing)
How to browse the web safely.
0:35 minutes
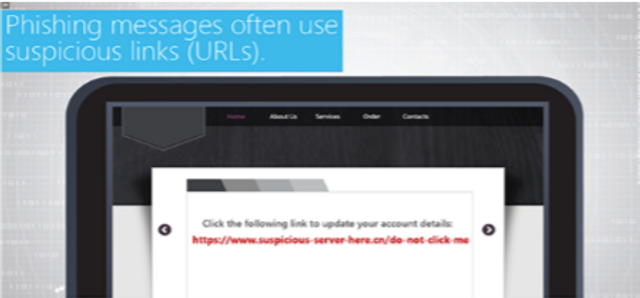
Suspicious Hosts Assessment (Google) W/ Hints
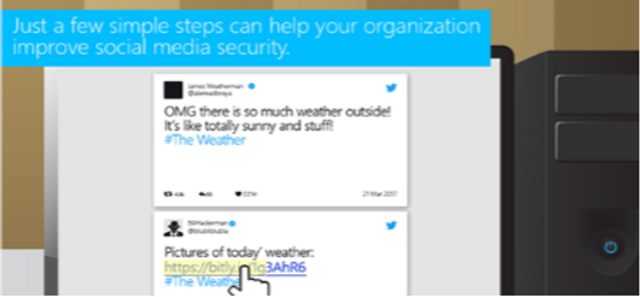
Safe Use of Social Media (Video)
Share Responsibly
Data Classification (Video)
This module discusses the importance of data security and how to classify data.
1:29 minutes
Personal Information (Video)

Secure Data Storage (Video)
Improper Error Handling
Errors are a fact of life in any system. But what happens when an error report ends up revealing a weakness? Take a closer look at the problem of improper error handling.
3:26 minutes

Acceptable Use Policy
When you start a new job or enroll in a new school, you’ll often be asked to review and sign an Acceptable Use Policy for the network. Let’s take a quick look at the purpose and contents of an AUP.
4:39 minutes

Buffer Overflow
This module discusses the risks caused by buffer overflows and how to avoid them.
2:56 minutes
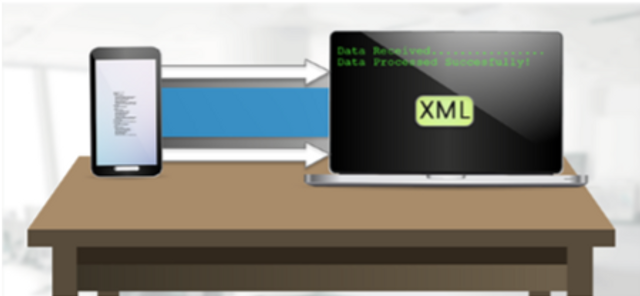
XML External Entitites (XXE)
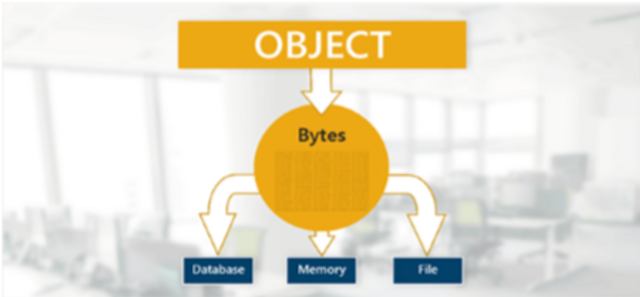
Insecure Deserialization
This module covers best practices for serialization - the process of turning data objects into binary streams of data.
4:06 minutes
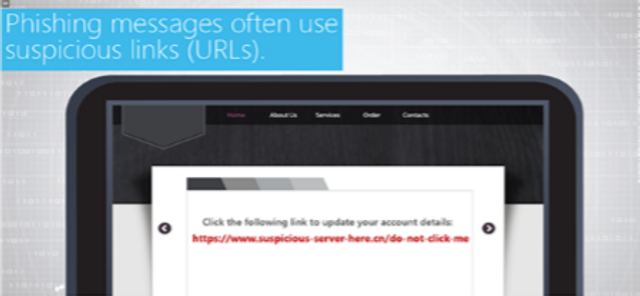
Suspicious Hosts

Top 25 #1 - SQL Injection
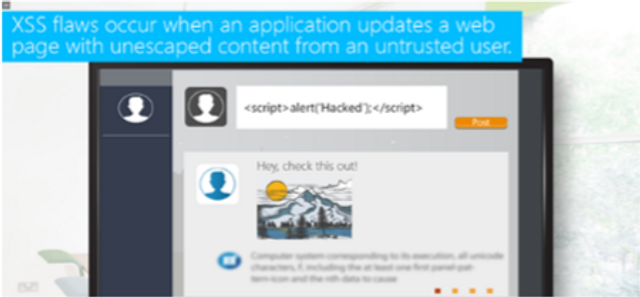
OWASP A7 - Cross-Site Scripting (XSS)
This module covers cross-site scripting.
4:18 minutes
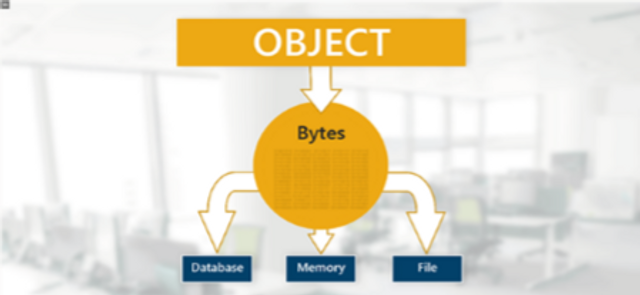
OWASP A8 - Insecure Deserialization
This module covers insecure deserialization vulnerabilities in applications and how to prevent these flaws.
4:11 minutes
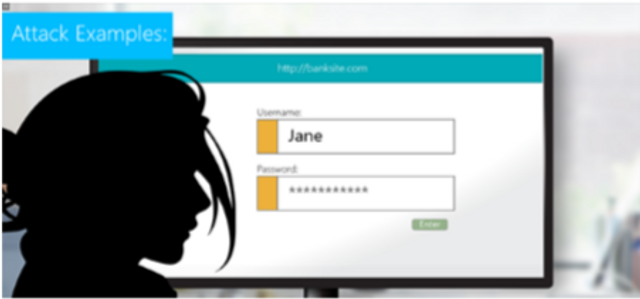
OWASP A5- Broken Access Control
This module covers broken access control, types of attacks and how to prevent them.
3:55 minutes
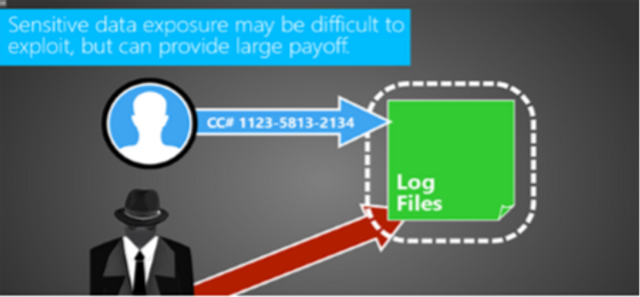
OWASP A3 - Sensitive Data Exposure
This module covers sensitive data and how to protect it.
5:31 minutes
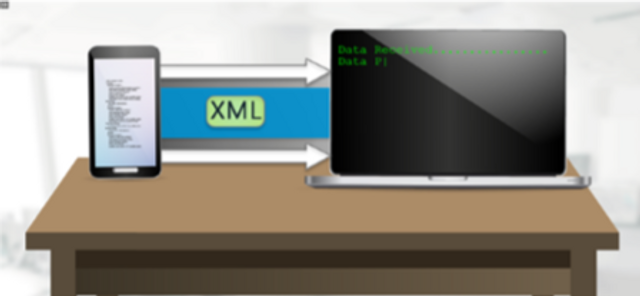
OWASP A4 - XML External Entities (XXE)
This module covers XML external entities, their flaws and how to protect them.
4:40 minutes
OWASP A2 - Broken Authentication
This module covers authentication vulnerabilities and session management.
6:05 minutes

OWASP A1 - Injection
This module covers various types of injection and the associated risks to applications
4:35 minutes

OWASP Top Ten Overview
This module will cover the Open Web Application Security Project’s list of the ten most dangerous Web application security flaws.
36:10 minutes
COPPA
This module covers the provisions of the Children’s Online Privacy Protection Act (COPPA), when an organization is subject to COPPA requirements, and how to ensure compliance with COPPA provisions.
6:11 minutes

CPNI for Providers
This security and awareness training covers Customer Proprietary Network Information, or CPNI.
7:56 minutes

Request your free demo today.
Please complete and submit the form below.


