Training
Training Courses
Course Catalog
*Courses may vary.
Search Courses

FERPA for Post-Secondary Education

The Family Educational Rights and Privacy Act (FERPA)

FERPA for K-12

HIPAA Minimum Necessary Standard (Video)

HIPAA/HITECH for Healthcare Executives

HIPAA/HITECH for Healthcare Managers
This module defines protected health information (PHI), outlines best practices for handling PHI and the responsibilities of healthcare managers in protecting PHI and ensuring HIPAA compliance.
14:21 minutes

Consequences of PHI Release
This brief video shows the possible consequences of a PHI breach at your organization.
1:45 minutes

PHI Policy (Video)
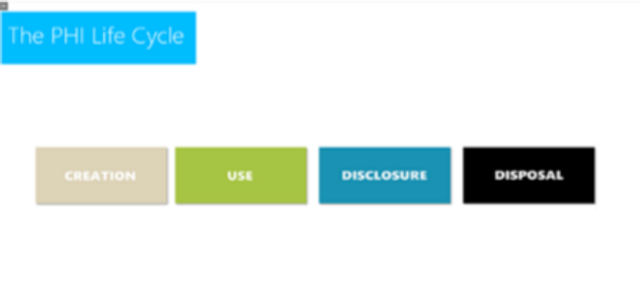
PHI Life Cycle (Video)

PHI Definition (Video)

Introduction To HIPAA (Video)

HIPAA HITECH
Election Security
What can you do to prevent election fraud? More than you may think! In one short video, you’ll explore the dos and don’ts of ensuring a safe and secure election process.
3:55 minutes

Privacy for HR

Privacy for Managers

Privacy for Executives.
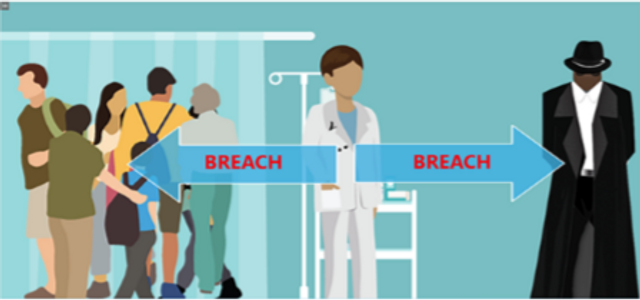
Breach Notification for Healthcare Managers
This module details HIPAA’s definition of a breach, breach disclosure requirements (including an overview of the concept of safe harbor) and recommended breach detection and notification methods.
8:54 minutes

Social Engineering for Financial Institutions

Social Engineering for Healthcare Managers

Social Engineering for Healthcare Executives

Social Engineering for Healthcare Professionals And Providers

Social Engineering for Educators

Social Engineering for Managers

Advanced Persistent Threat (APT)
This module explains how to recognize advanced persistent threats (APT), APT risks and common attack methods.
7:22 minutes
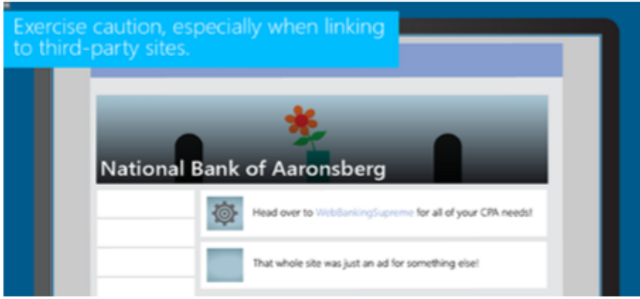
Social Media for Financial Institutions

Request your free demo today.
Please complete and submit the form below.


