Removable Media and PHI for Executives
This module details best practices healthcare executives can implement across their organizations to safeguard protected health information and avoid infection from removable media.
9:13 minutes
*Courses may vary.
Search Courses

This module details best practices healthcare executives can implement across their organizations to safeguard protected health information and avoid infection from removable media.
9:13 minutes

This module details best practices healthcare managers can follow to safeguard protected health information and avoid infection from removable media.
9:59 minutes



HIPAA includes specific requirements for physical safeguards that every organization should have in place to secure protected health information (PHI).
10:19 minutes
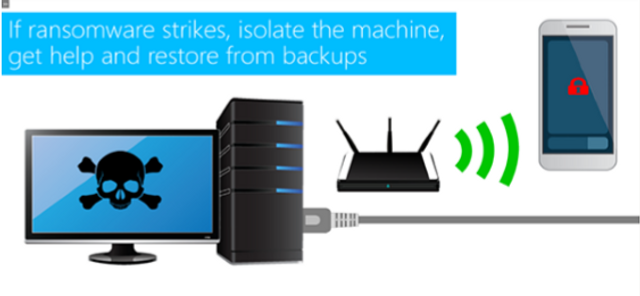

This training outlines steps healthcare executives can take to proactively keep PHI secure. Suggested security policies and staff communication strategies are also introduced in this module.
9:11 minutes

This training outlines steps healthcare managers can take to proactively keep PHI secure. Suggested security policies and staff communication strategies are also introduced in this module.
10:25 minutes

Malware infections are considered a HIPAA security incident. This module teaches healthcare professionals how to identify malware and actions organizations can take to avoid malware infections.
9:36 minutes

This security awareness module covers best practices for ensuring HIPAA compliance when using mobile devices to store or access protected health information.
7:32 minutes
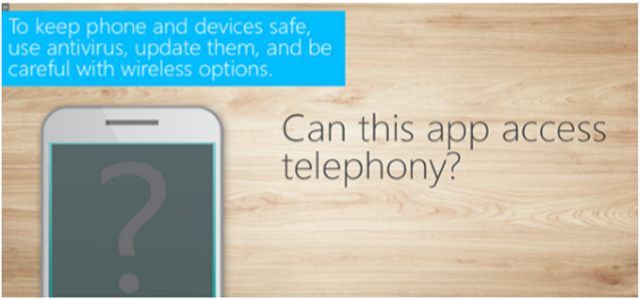
In this module, we review the risks of conducting business on mobile devices and public networks, and share best practices for working remotely at home and abroad.
6:49 minutes

This security awareness module covers best practices for healthcare professionals to ensure HIPAA compliance when using mobile devices to store or access protected health information.
7:02 minutes

This brief video extrapolates on how many people are authorized to access one person’s health records.
1:54 minutes

This module defines protected health information (PHI), outlines best practices for handling PHI, and explains the role healthcare executives play in ensuring HIPAA compliance by employees.
14:06 minutes

This module defines protected health information (PHI), outlines best practices for handling PHI and the responsibilities of healthcare managers in protecting PHI and ensuring HIPAA compliance.
14:21 minutes

This brief video shows the possible consequences of a PHI breach at your organization.
1:45 minutes



This module briefly covers the main points of HIPAA compliance.
1:23 minutes

Our role-based HIPAA/HITECH module defines Protected Health Information (PHI), explains the need for PHI security and outlines best practices for handling PHI.
14:16 minutes
This module details HIPAA’s definition of a breach, breach disclosure requirements (including an overview of the concept of safe harbor) and recommended breach detection and notification methods.
8:54 minutes


This module explains the social engineering methods hackers use, review HIPAA requirements regarding external requests for PHI, and teach managers to work with staff to prevent PHI breaches and leaks.
8:49 minutes

Healthcare professionals are targeted by hackers via social engineering. This module will explain social engineering techniques in detail, and review HIPAA requirements regarding external requests for PHI.
9:33 minutes
This module will explain safe browsing best practices, and provide guidance for executives to implement and enforce safe-browsing policies to avoid exposure of protected health information.
12:58 minutes

Please complete and submit the form below.

