Conclusion
This module will review critical lessons from your security awareness training to increase team retention of core program content.
2:05 minutes
*Courses may vary.
Search Courses
This module will review critical lessons from your security awareness training to increase team retention of core program content.
2:05 minutes

The module will outline cyber threats (established and emerging), recent attacks and industry regulations, and also position employees as key players in modern cybersecurity initiatives.
5:13 minutes












Our Social Engineering module teaches a three-step method to add clarity to a confusing conversation, challenge the other person’s identity and verify suspicious requests.
12:54 minutes
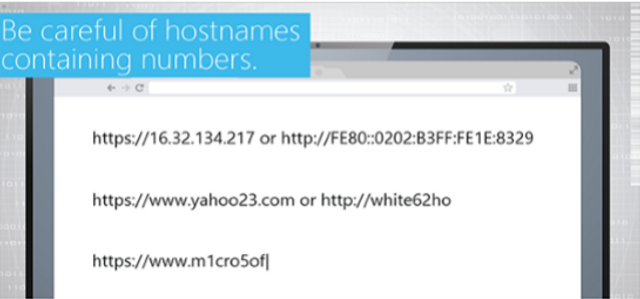

This interactive module covers two key areas of focus: safe use of removable media for legitimate purposes, and types of attacks hackers launch from “lost” removable media.
10:47 minutes


Sometimes, trouble follows you home. Join in as Anthony and Ben explore the dangers of working remotely — from password cracks to malware attacks.
3:20 minutes

Some hackers don’t need computers at all. Join Anthony and Erica in exploring the dirty business of social engineering — when all it takes is a lie to crack open a company.
4:05 minutes

It’s a jungle in there. Explore the winding paths of the internet with Anthony and Cecil as they venture into thorny areas like fake browser warnings, HTTPS and dangerous URLs.
3:54 minutes

Can a thumb drive topple a company? It’s more likely than you think. Join Anthony and Harold as they check out the dangers of removable media — the good, the bait and the ugly.
2:52 minutes

Anthony and his pal Harold talk physical security. Why do you secure everything (even the printer), and what could someone get by sneaking in? Here’s how not to leave security out in the cold.
4:15 minutes

Learn how to spot the bait as Anthony guides his friend Cecil through the dangers of phishing. Is this actually a very exciting email from the boss, or is it just another hacker’s trap?
4:40 minutes

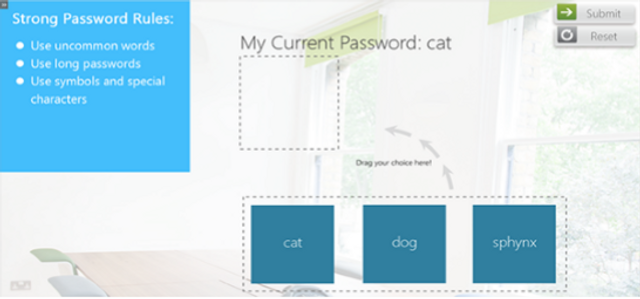
A system is only as secure as its password. Join Anthony and Daryl as they get to grips with the challenges of creating a strong password … because safety is not as easy as 1-2-3.
3:51 minutes

Join Anthony and Ivana as they explore the ups and downs of phone security. What is encryption? What kind of damage could a stolen phone do? Learn how to take security with you wherever you go.
3:32 minutes

Please complete and submit the form below.

