Conclusion
This module will review critical lessons from your security awareness training to increase team retention of core program content.
2:05 minutes
*Courses may vary.
Search Courses
This module will review critical lessons from your security awareness training to increase team retention of core program content.
2:05 minutes

The module will outline cyber threats (established and emerging), recent attacks and industry regulations, and also position employees as key players in modern cybersecurity initiatives.
5:13 minutes

Spearphishing occurs when phishing messages are tailored for targeted individuals. This interactive module will help teams identify and avoid spearphishing attempts.
2:40 minutes

Our Social Engineering module teaches a three-step method to add clarity to a confusing conversation, challenge the other person’s identity and verify suspicious requests.
12:54 minutes
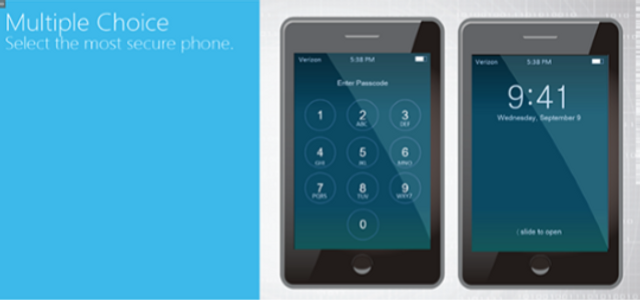


This module highlights the importance of using secure connections when sending sensitive data over the Internet.
0:35 minutes
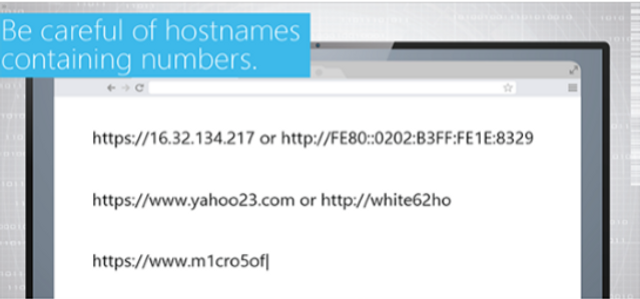
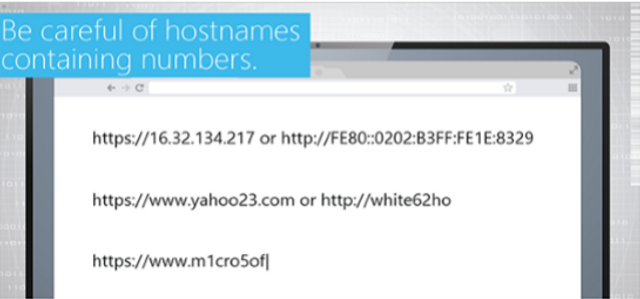


This summary course gives learners a basic understanding of the risks associated with removable media and how to avoid infection from these devices.
2:06 minutes

This interactive module covers two key areas of focus: safe use of removable media for legitimate purposes, and types of attacks hackers launch from “lost” removable media.
10:47 minutes
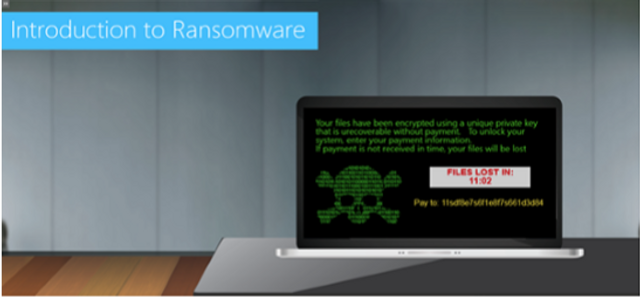
Ransomware is malware that holds technology for ransom. This module will show learners how ransomware works, what do if an infection occurs, and how to avoid future infections.
4:38 minutes




This module will introduce learners to the concept of phishing, teach them how to quickly identify phishing messages and show them how to verify whether or not a message is legitimate.
2:49 minutes
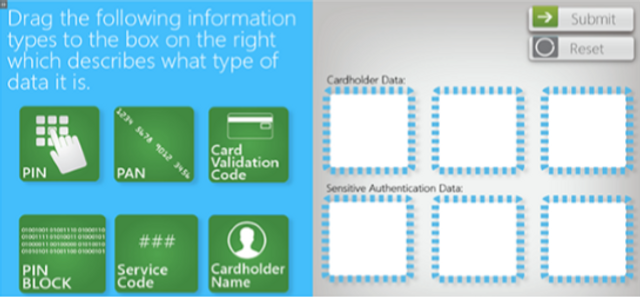
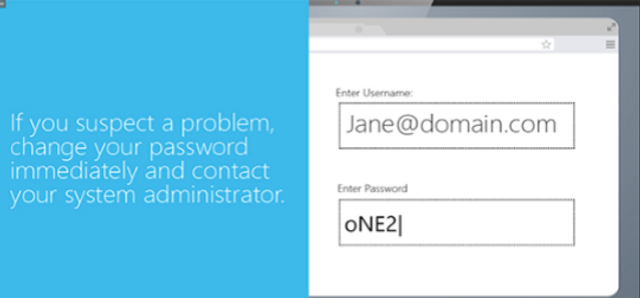
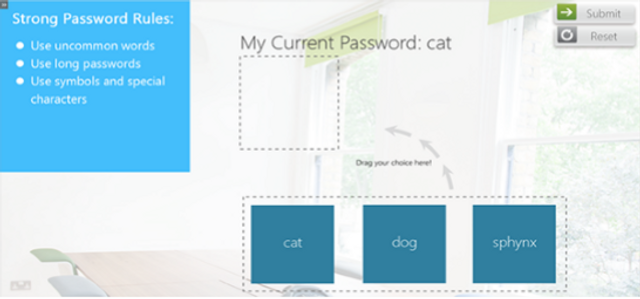

This one-minute video shows the consequences of a phishing attack.
1:00 minutes
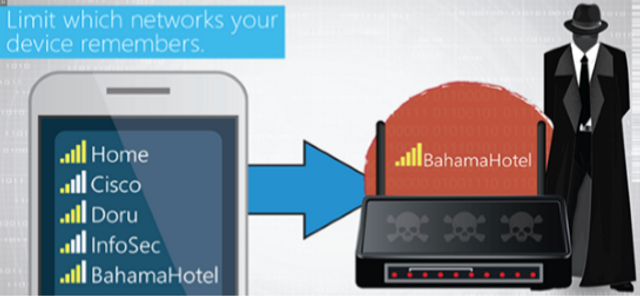
Our Mobile Wi-Fi Security module explains how to safely use wireless devices when operating on Wi-Fi connections.
2:07 minutes
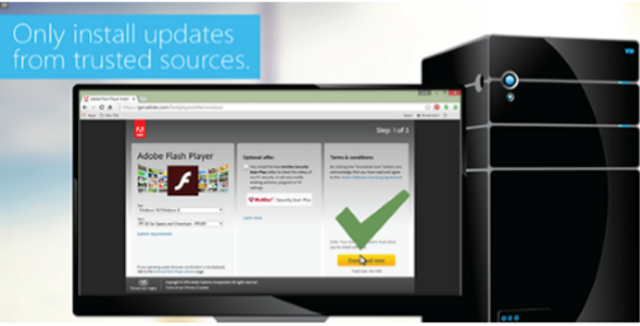
This module focuses on three key ways to prevent malware infections, details common sources of malware infections and discusses methods to help users avoid unsafe files.
3:21 minutes

This interactive module defines malware in common terms, details the dangers it poses to organizations, and discusses preventative actions.
17:01 minutes

Please complete and submit the form below.

