Training
Training Courses
Course Catalog
*Courses may vary.
Search Courses

Phishing In Brief
This module will introduce learners to the concept of phishing, teach them how to quickly identify phishing messages and show them how to verify whether or not a message is legitimate.
2:49 minutes
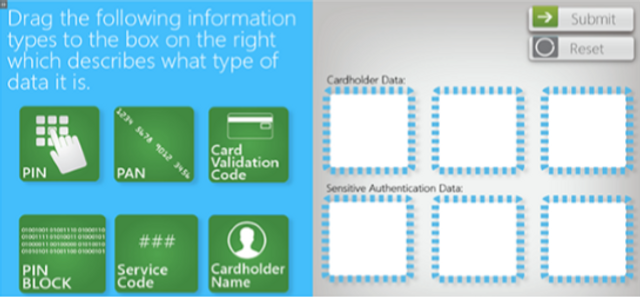
PCI DSS Brief
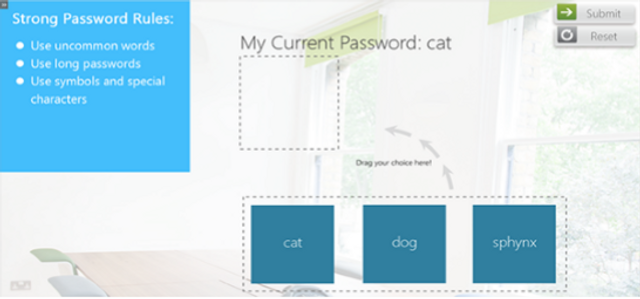
Password Security

One Wrong Move (Phishing)
This one-minute video shows the consequences of a phishing attack.
1:00 minutes

Need to Know: Working Remotely
Sometimes, trouble follows you home. Join in as Anthony and Ben explore the dangers of working remotely — from password cracks to malware attacks.
3:20 minutes

Need to Know: Social Engineering
Some hackers don’t need computers at all. Join Anthony and Erica in exploring the dirty business of social engineering — when all it takes is a lie to crack open a company.
4:05 minutes

Need to Know: Safe Web Browsing
It’s a jungle in there. Explore the winding paths of the internet with Anthony and Cecil as they venture into thorny areas like fake browser warnings, HTTPS and dangerous URLs.
3:54 minutes

Need to Know: Removable Media
Can a thumb drive topple a company? It’s more likely than you think. Join Anthony and Harold as they check out the dangers of removable media — the good, the bait and the ugly.
2:52 minutes

Need to Know: Physical Security
Anthony and his pal Harold talk physical security. Why do you secure everything (even the printer), and what could someone get by sneaking in? Here’s how not to leave security out in the cold.
4:15 minutes

Need to Know: Phishing
Learn how to spot the bait as Anthony guides his friend Cecil through the dangers of phishing. Is this actually a very exciting email from the boss, or is it just another hacker’s trap?
4:40 minutes

Need to Know: Password Security
A system is only as secure as its password. Join Anthony and Daryl as they get to grips with the challenges of creating a strong password … because safety is not as easy as 1-2-3.
3:51 minutes

Need to Know: Mobile Security
Join Anthony and Ivana as they explore the ups and downs of phone security. What is encryption? What kind of damage could a stolen phone do? Learn how to take security with you wherever you go.
3:32 minutes
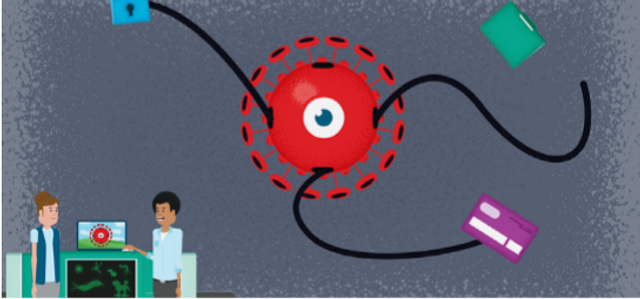
Need to Know: Malware
Trojan horses, worms, RATs — There’s a whole animal kingdom of malware out there. Join Anthony and Fiona as they explore the best ways to keep malware from migrating into your system.
3:50 minutes

Need to Know: Conclusion
Take a moment to relax and review what you’ve learned as Anthony takes you through a few simple cybersecurity principles. Congratulations on completing your training!
2:25 minutes

Need to Know: Introduction
Begin at the beginning as Anthony introduces you to our plan for what’s to come. Let’s talk about hackers, cybersecurity, and why it pays to keep a good head on your shoulders.
1:44 minutes
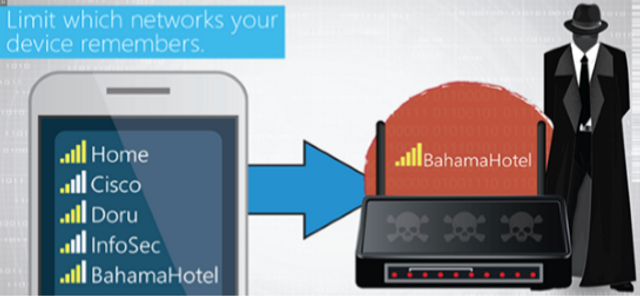
Mobile Wi-Fi Security
Our Mobile Wi-Fi Security module explains how to safely use wireless devices when operating on Wi-Fi connections.
2:07 minutes
Malware Brief
This module focuses on three key ways to prevent malware infections, details common sources of malware infections and discusses methods to help users avoid unsafe files.
3:21 minutes

Malware
This interactive module defines malware in common terms, details the dangers it poses to organizations, and discusses preventative actions.
17:01 minutes

Is It Safe? (Mobile Security)
This short video reinforces the importance of using trusted publishers when installing mobile applications.
1:00 minutes

How Secure Is Public WiFi? (Public WiFi)
In just one minute, this video explains the risks of connecting to public Wi-Fi networks, including how sensitive information can be intercepted by attackers.
1:00 minutes

How Much Is Too Much? (Password Security)
In less than one minute, this video reinforces the importance of keeping passwords private.
1:00 minutes

Avoiding Cybersecurity Risks for Executives
This security awareness module explains why top-level managers are targeted by malicious hackers, details common attack methods, and offers recommendations for avoiding security risks.
9:45 minutes

Request your free demo today.
Please complete and submit the form below.


