Conclusion
This module will review critical lessons from your security awareness training to increase team retention of core program content. 2:05 minutes
*Courses may vary.
Search Courses


Spearphishing occurs when phishing messages are tailored for targeted individuals. This interactive module will help teams identify and avoid spearphishing attempts.
2:40 minutes

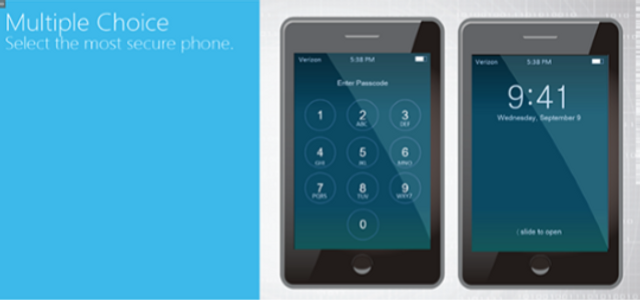


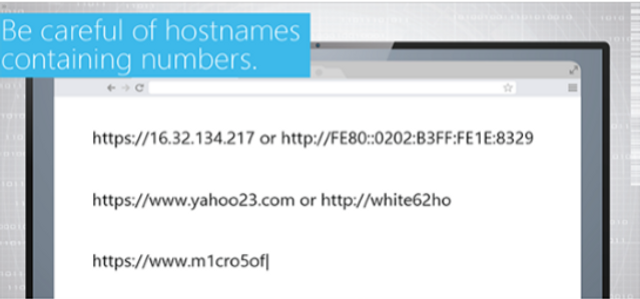
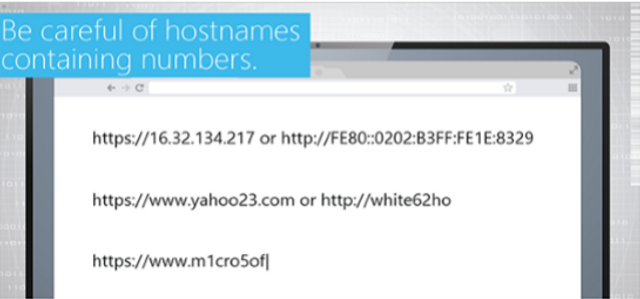



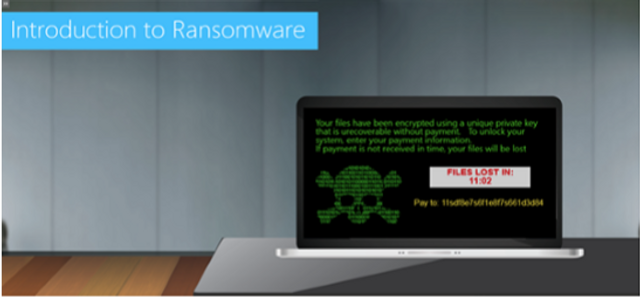




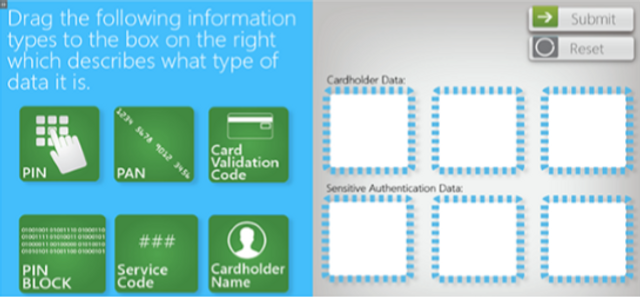
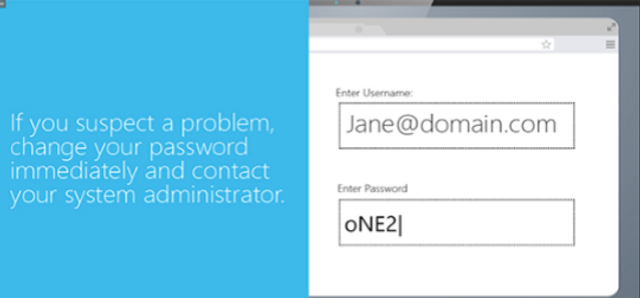
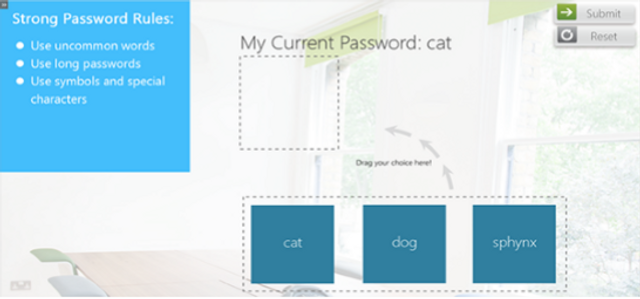

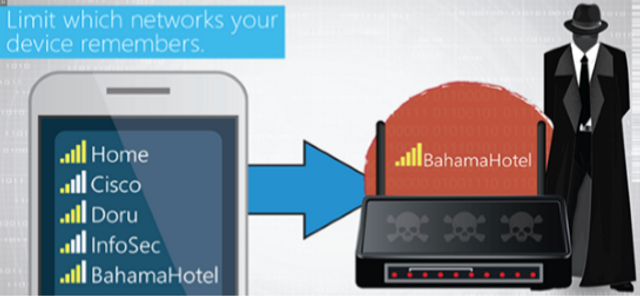


Please complete and submit the form below.

