Training
Training Courses
Course Catalog
*Courses may vary.
Search Courses

Removable Media and PHI for Healthcare Managers

Physical Security and PHI for Healthcare Managers

Physical Security and PHI for Healthcare Executives

Physical Security and PHI
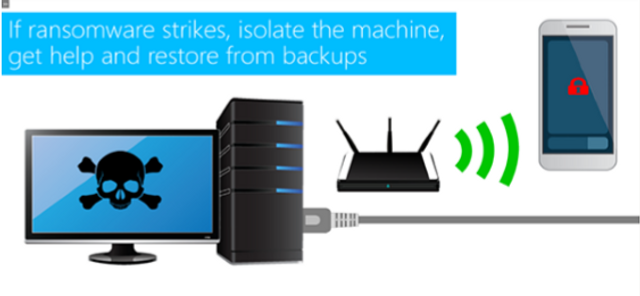
Ransomware and HIPAA

Malware and PHI for Managers

Malware and PHI for Executives

Malware and PHI
Malware infections are considered a HIPAA security incident. This module teaches healthcare professionals how to identify malware and actions organizations can take to avoid malware infections.
9:36 minutes

Mobile Security for Healthcare Managers
This security awareness module covers best practices for ensuring HIPAA compliance when using mobile devices to store or access protected health information.
7:32 minutes
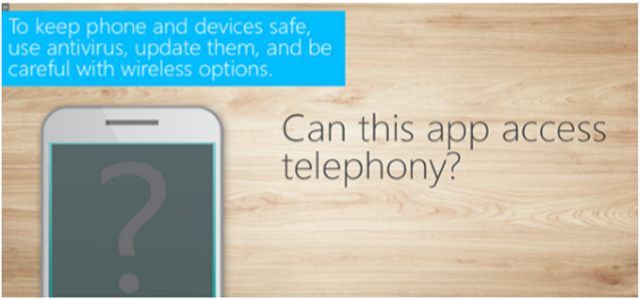
Mobile Security for Healthcare Executives
In this module, we review the risks of conducting business on mobile devices and public networks, and share best practices for working remotely at home and abroad.
6:49 minutes

Mobile Security for Healthcare Professionals
This security awareness module covers best practices for healthcare professionals to ensure HIPAA compliance when using mobile devices to store or access protected health information.
7:02 minutes

HIPAA Minimum Necessary Standard (Video)
This brief video extrapolates on how many people are authorized to access one person’s health records.
1:54 minutes

HIPAA/HITECH for Healthcare Executives
This module defines protected health information (PHI), outlines best practices for handling PHI, and explains the role healthcare executives play in ensuring HIPAA compliance by employees.
14:06 minutes

HIPAA/HITECH for Healthcare Managers
This module defines protected health information (PHI), outlines best practices for handling PHI and the responsibilities of healthcare managers in protecting PHI and ensuring HIPAA compliance.
14:21 minutes

Consequences of PHI Release
This brief video shows the possible consequences of a PHI breach at your organization.
1:45 minutes

PHI Policy (Video)
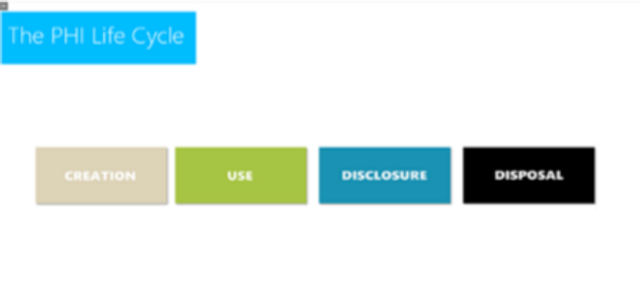
PHI Life Cycle (Video)

PHI Definition (Video)

Introduction To HIPAA (Video)
This module briefly covers the main points of HIPAA compliance.
1:23 minutes

HIPAA HITECH
Our role-based HIPAA/HITECH module defines Protected Health Information (PHI), explains the need for PHI security and outlines best practices for handling PHI.
14:16 minutes
Breach Notification for Healthcare Managers
This module details HIPAA’s definition of a breach, breach disclosure requirements (including an overview of the concept of safe harbor) and recommended breach detection and notification methods.
8:54 minutes

Social Engineering for Healthcare Managers

Social Engineering for Healthcare Executives

Social Engineering for Healthcare Professionals And Providers
Safe Web Browsing for Healthcare Executives

Request your free demo today.
Please complete and submit the form below.


