Training
Training Courses
Course Catalog
*Courses may vary.
Search Courses

Phishing Assessment (Capital One) W/ Hints

Suspicious Hosts Assessment (Google)
Phishing Assessment (LinkedIn)

Phishing Assessment (Capital One)

Breach Notification
This module details best practices for detecting and reporting unauthorized Protected Health Information (PHI) disclosures.
8:14 minutes
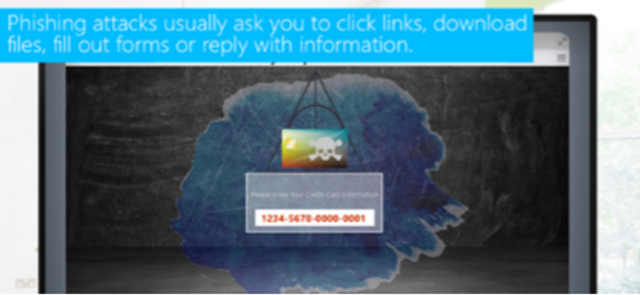
Recognizing Phishing Emails (Video)

What Is Phishing? (Video)

EAL Phishing
This module teaches learners how to avoid falling victim to phishing.
2:11 minutes
Phishing for Financial Institutions

Phishing for Healthcare Executives

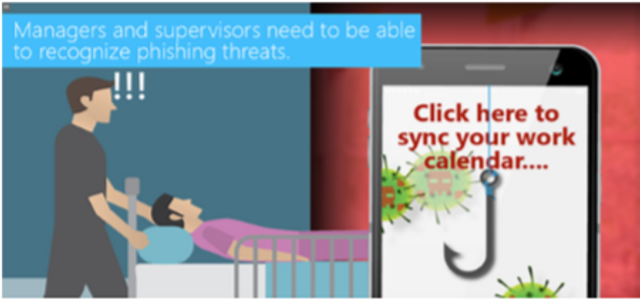
Phishing for Healthcare Managers
Phishing for Healthcare Professionals and Providers

Phishing for Educators

Phishing for Executives
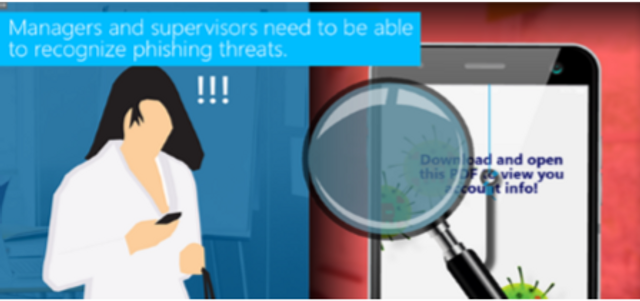
Phishing for Managers

Marine Lowlifes: Spearphish
Target sighted! Follow the hunt of that vicious but sometimes misaimed predator, the Spearphish.
1:30 minutes

Marine Lowlifes: Whaling Shark
The wonders of nature are displayed up close as the Whaling Shark chases its prey, the powerful and important Whale.
1:23 minutes

Marine Lowlifes: Common Phish
Dive into the Sea of Emails for a closer look at one of the oldest scams still swimming today: the Common Phish.
1:25 minutes

Marine Lowlifes: Clone Phish
Sink into the depths to observe the Clone Phish, which disguises itself as a previously trustworthy message to lure in prey.
1:18 minutes

WORKed Episode 2: Evite

Vishing
This interactive training module covers voice phishing, or vishing, a simple but effective technique cybercriminals and scam artists use to collect confidential information.
6:44 minutes

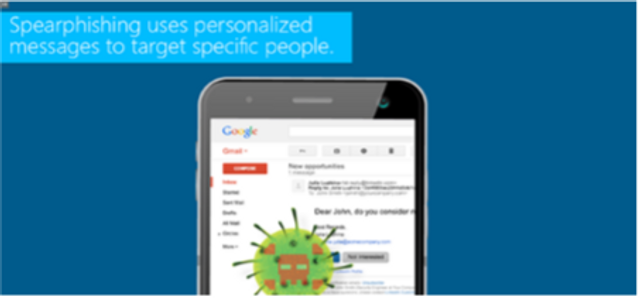
Spearphishing
Spearphishing occurs when phishing messages are tailored for targeted individuals. This interactive module will help teams identify and avoid spearphishing attempts.
2:40 minutes
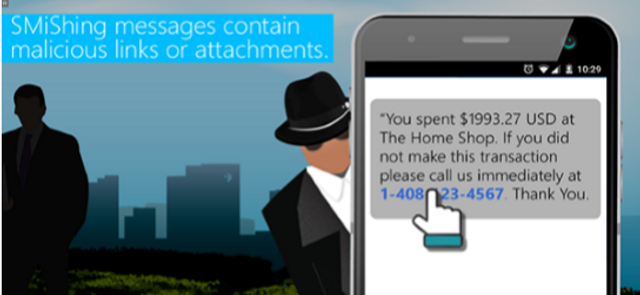
SMiShing
SMS Phishing, or SMiShing, is used by cybercriminals to collect valuable information and distribute malware. This module includes effective ways to stop SMiShing attempts.
4:58 minutes
Reporting Phishing Emails

Phishing In Brief

Request your free demo today.
Please complete and submit the form below.