What Is Microservices Security and Why It Matters
What Is Microservices Security and Why It Matters
As a security expert, keeping up with new technology is part of the job. Today, systems change fast. New terms like cloud-native, loosely coupled systems, and continuous integration are now common. Many organizations are moving from monolithic applications to smaller, modular setups. These changes bring benefits but also new security issues. Companies now manage both old systems and new ones. To build strong microservices security, you need to understand both.
Think of microservices like different departments in a company—HR, finance, and sales—each performing their own role independently but collaborating to keep the organization running efficiently. This is like how microservices contribute individually to the full functionality of an application.
This article explains what microservices are. It shows why they are popular, what risks they bring, and how to protect them.
What Are Microservices?
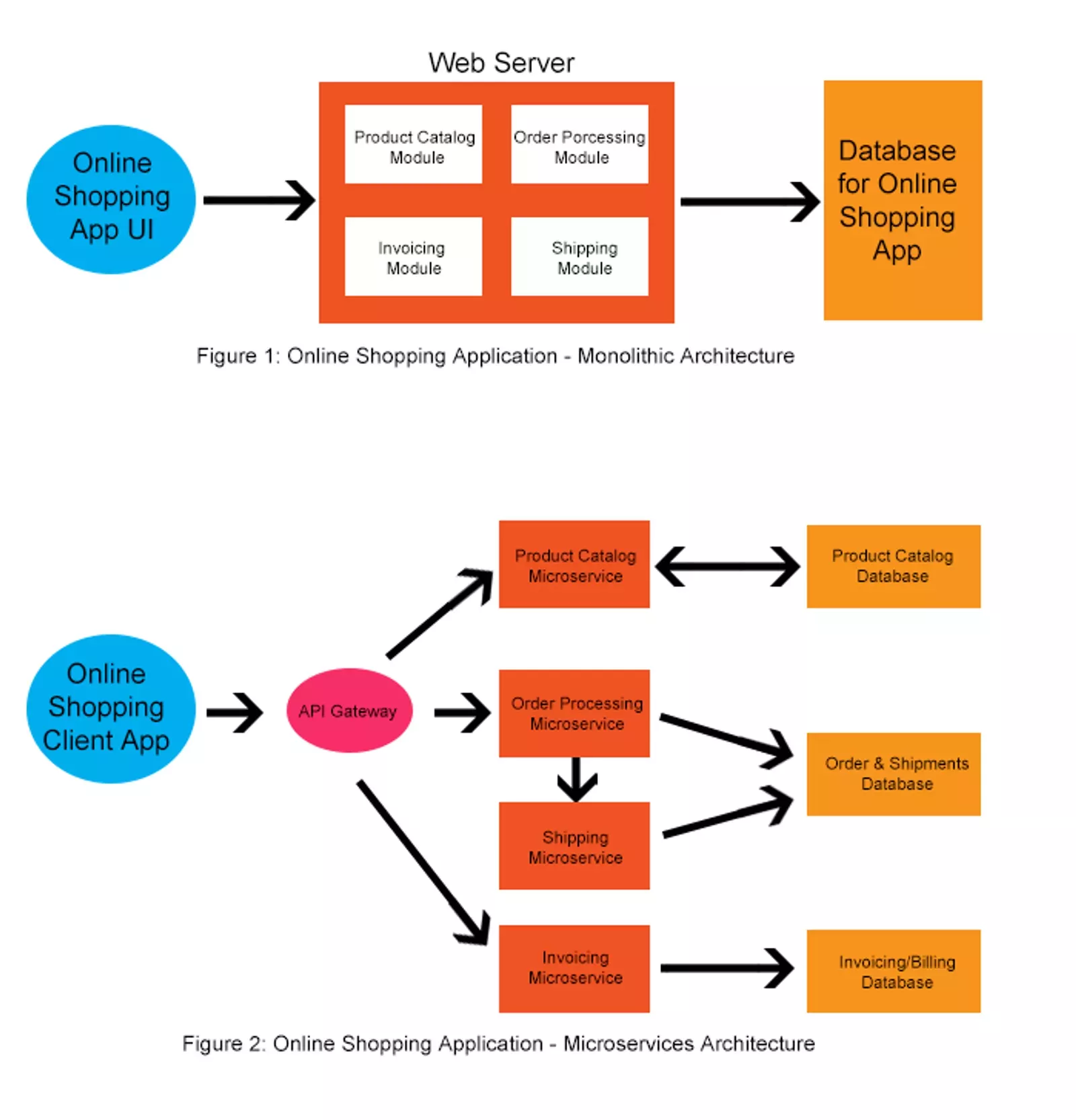
Microservices are small, independent tools inside an app. Each one does a single job. They talk to each other using inter-service communication methods like Application Programming Interface (API)s or messaging tools such as Kafka. They can run on different platforms and use any programming language.
Using microservices security practices early in development is key. This means setting clear rules for each service to follow.
Benefits of microservices include:
- Flexibility with different tools and systems
- Services can be deployed and updated on their own
- Failures stay isolated
- Faster development with Continuous Delivery (CD) pipelines and continuous integration
How do Microservices Work?
Microservices are a software development approach that structures an application as a collection of small, independent services. Each service is designed to perform a specific task and can be developed, tested, and deployed independently. This approach allows for greater flexibility, scalability, and resilience compared to traditional monolithic architectures. In a microservices architecture, each service communicates with others using lightweight protocols and APIs, enabling seamless interaction and data exchange.
However, this distributed nature also introduces unique security challenges, such as securing inter-service communication, managing access controls, and protecting sensitive data.
Benefits and Challenges of Microservices
Microservices can greatly enhance application flexibility and speed but also introduce new layers of complexity. Understanding both the advantages and disadvantages is essential to make informed design and security decisions.
Key Advantages:
- Scalability: Each service can grow or shrink based on needs. API gateways manage traffic, enforce rate limiting, and check user IDs.
- Fault Isolation: One broken part won't break the full app. Keeping services secure protects your data.
- Flexibility: Teams can build services using different tools.
- Real-Time Updates: You can release improvements faster in real-time.
Disadvantages:
- Hard to Monitor: You need special tools to track many services. Service mesh tools help by tracking traffic and usage.
- Version Control: Different versions may run at the same time, causing problems.
- Security Risks with APIs: Data moves over networks, not inside one program. Use Transport Layer Security (TLS) and authentication and authorization controls.
- Rate Limiting Gaps: Without it, APIs could be attacked.
Specific Security Threats in Microservices
Microservices inherit all traditional application security vulnerabilities, think the OWASP Top Ten, but introduce unique threats:
- Fake Services: Use strong ID checks and multi-factor authentication (MFA).
- Bigger Attack Surface: More services mean more ways in. Don't hard-code secrets in code. Use secrets management tools.
- Unprotected Traffic: Services must secure east-west traffic between them using TLS and JavaScript Web Tokens (JWT).
- Different Security Rules: Inconsistent rules create weak points. Use shared common security practices.
Additional threats include:
- Insufficient Logging and Monitoring: Without robust logging and monitoring, it’s hard to detect unauthorized access or service misuse. Implementing centralized logging improves visibility.
- Insecure CI/CD Pipelines: If the CI/CD pipeline is compromised, attackers can introduce malicious code into the deployment. Protect the pipeline with signed containers, validation checks, and restricted access.
How to Secure Microservices
Securing microservices requires a different approach than traditional application models. Since these services are distributed, loosely connected, and often independently deployed, it's important to apply layered, adaptive security measures throughout the system lifecycle.
- API Gateway: Controls traffic and access. It can block bad requests and enforce rules.
- Service Mesh and Data Flow Maps: Shows how data moves. It helps you know where to apply security. Tools make your services work together safely.
- Encrypt All Data: Use TLS for all messages, not just for user logins.
- Central Monitoring: Use tools to track all services in one place. Add circuit breakers to avoid chain reactions.
- Strong Identity Checks: Use authentication and authorization keys to control access.
Securing Microservices
Securing microservices requires a comprehensive approach that addresses the unique security challenges introduced by this design. One key strategy is to implement a service mesh, which provides a configurable infrastructure layer for microservices communication. This allows for features like encryption, authentication, and rate limiting to be applied consistently across all services.
Additionally, using an API gateway as a single-entry point for client requests can help control access, prevent unauthorized access, and protect against data breaches. Implementing robust security measures, such as dynamic analysis security testing and static analysis security testing, is also crucial for identifying and mitigating security risks.
Adopting a zero-trust model, which assumes nothing in the network is trusted by default, adds further resilience. This ensures that all identities are verified before accessing any service. Additionally, aligning your system with compliance standards like SOC 2 or ISO/IEC 27001 builds confidence with customers and regulators alike.
East West Traffic
Securing internal communication between microservices, known as "east-west traffic," is vital for preventing unauthorized access and data breaches in distributed systems. Techniques such as mutual TLS and JWT are used to authenticate and authorize service-to-service communication. Implementing a service mesh can provide features like automatic traffic encryption and fine-grained access controls, enhancing security.
Furthermore, employing access tokens and adhering to the principle of least privilege are key strategies for controlling access and minimizing the risk of exposing sensitive data. Establishing strong security for east-west traffic is fundamental to maintaining a resilient and secure distributed environment.
Cloud Native Services
When you build a system using lots of small, independent parts (that's a "microservices architecture"), cloud-native services offer a secure and flexible way to put those parts into action and keep them running smoothly.
Cloud companies provide a bunch of security tools to help protect these microservices. This includes things like managing who can access what (identity and access management), securing the connections between services (network security), and scrambling data to keep it private (encryption).
Popular cloud-native tools include:
- AWS IAM for fine-grained identity and permissions management
- Azure Policy for automating governance and compliance
- GCP Cloud Armor for shielding services against denial-of-service (DoS) and other attacks
Plus, cloud-native services often have built-in ways to keep track of what's happening and monitor for any problems. This makes it easier to spot security issues and keep a record of important activities for security checks (logging and auditing).
Conclusion
Microservices help apps grow and change faster, but they also bring new risks. By prioritizing security and implementing adequate security measures, organizations can ensure the integrity and confidentiality of sensitive data and maintain a heightened security posture. Regularly reviewing and updating security measures is also essential to stay ahead of evolving security risks and threats.
At TechGuard, we help secure modern apps. We offer tools and services for microservices security. We focus on cloud-native platforms, service mesh tools, and rate limiting. We protect your systems from risks and make sure you meet rules and standards. Our expert team works with you to build a customized plan for your app’s needs.
We understand the nature of microservices and the critical need for secure, scalable application architectures. Microservices security is important due to its critical role in maintaining system integrity and protecting sensitive data. Our team of experts provides customized microservices security solutions that align with your organization’s operational and regulatory needs.
Explore our full service offerings today and contact us to learn how we can help you secure the next generation of applications with confidence.