Training
Phishing Simulator and Training
91% of cyber-attacks begin with a phishing email.
That’s why our training includes Phishing courses as well as a Phishing Simulator to educate your employees through real-world scenarios. Empower them to make security-conscious decisions and report phishing attacks.
Know the Signs.
- Do not trust emails requesting personal or confidential information. Most companies will never ask for credentials via email.
- Beware of emails demanding urgent action.
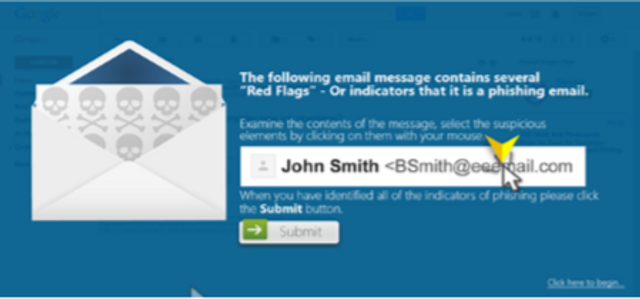
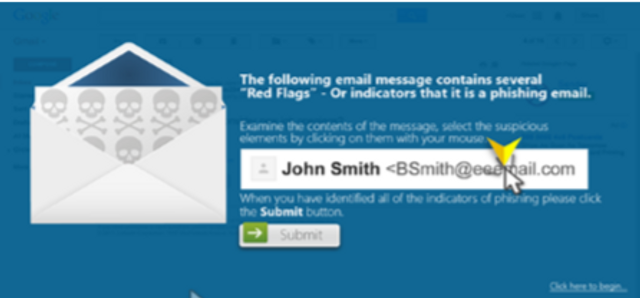
- Do not trust the display name. Cybercriminals will often spoof the display name of an email to impersonate a brand or person.
- Suspicious emails often have attachments and links. Never click any attachments or links in an email until you can verify the sender.
Phishing Simulator
An easy-to-use phishing simulator that delivers real-world scenarios for reinforcing phishing attack prevention and remediation for susceptible users.
- Unlimited phishing simulations
- 1,000+ customizable email templates
- Identify susceptible users & compare performance over time
- G-Suite & Outlook add-in
- Campaign randomizer
- Automatically assign courses for remediation
- Educational landing pages
- USB drop campaigns
Phishing Outlook and G-Suite Add-in
Outlook and G-Suite add-in to ensure employees know exactly what to do when they come across a suspicious email.
- Employees receive immediate positive reinforcement at the time of identification of a simulated phishing attack
- If the threat didn’t come from our phishing simulator; the phishing add-in immediately sends a notification to alert the system administrator
- Proven to increase efficiency in identifying suspect phishing e-mails
- A simple and effective tool that empowers users
- Decreases the risk of network infections and intrusions

Request your free demo today.
Please complete and submit the form below.