Malware and PHI for Managers
This training outlines steps healthcare managers can take to proactively keep PHI secure. Suggested security policies and staff communication strategies are also introduced in this module.
10:25 minutes
*Courses may vary.
Search Courses

This training outlines steps healthcare managers can take to proactively keep PHI secure. Suggested security policies and staff communication strategies are also introduced in this module.
10:25 minutes

Malware infections are considered a HIPAA security incident. This module teaches healthcare professionals how to identify malware and actions organizations can take to avoid malware infections.
9:36 minutes

Executives are often targeted by hackers via malware, or malicious software. This module explains malware risks in detail and outlines steps executives can take to proactively keep their data secure.
7:23 minutes

This module will help managers understand the risks of malware, how to prevent installation and provide guidance on how managers can help their team and comply with internal security policies.
8:41 minutes



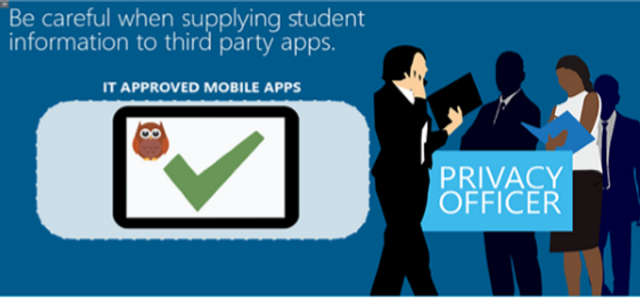
This module identifies the security risks educational institutions face from business-based mobile device use.
6:00 minutes
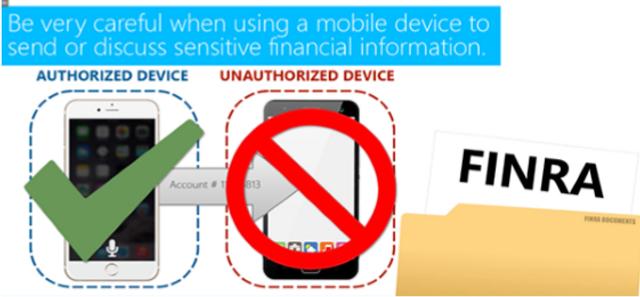
This module identifies the security risks financial institutions face from business-based mobile device use, malicious applications designed to attack financial accounts and possible FINRA violations.
6:31 minutes

This security awareness module covers best practices for ensuring HIPAA compliance when using mobile devices to store or access protected health information.
7:32 minutes
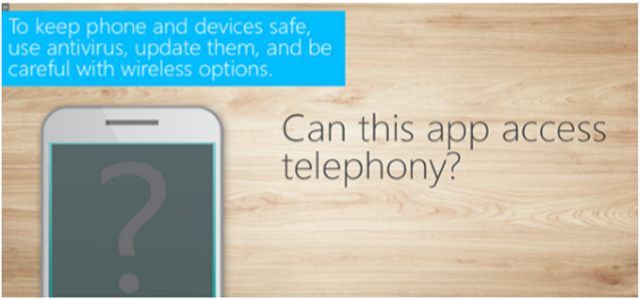
In this module, we review the risks of conducting business on mobile devices and public networks, and share best practices for working remotely at home and abroad.
6:49 minutes

This security awareness module covers best practices for healthcare professionals to ensure HIPAA compliance when using mobile devices to store or access protected health information.
7:02 minutes

This module will explain the risks of mobile devices and public networks in detail, and provide guidance on how managers can work with their teams to keep sensitive data secure.
7:03 minutes

In this module, we review the risks of conducting business on mobile devices and public networks, and share best practices for working remotely at home and abroad.
6:05 minutes

This module emphasizes the need to verify wire transfers.
1:00 minutes

h@ckj0b is your security team’s worst nightmare come to life. Will TechniCorp Dynamix survive Vermintooth’s assault, or will Tim leave them to deal with the mess they’ve gotten themselves into?
5:28 minutes

After you’ve learned good security practices, you should share your knowledge with others.
0:35 minutes

This micro-learning module emphasizes the importance of verifying wire transfers.
0:35 minutes

Security training should be a part of your daily life.
0:35 minutes
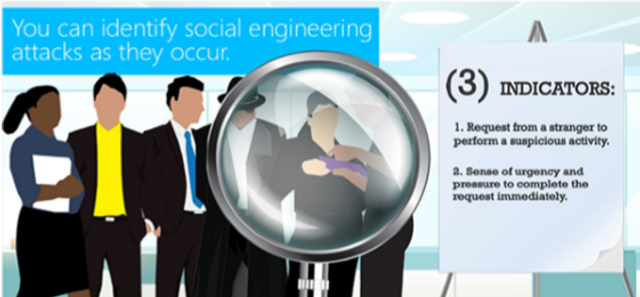
This brief overview covers the hallmarks of social engineering attacks and how to prevent them.
1:29 minutes
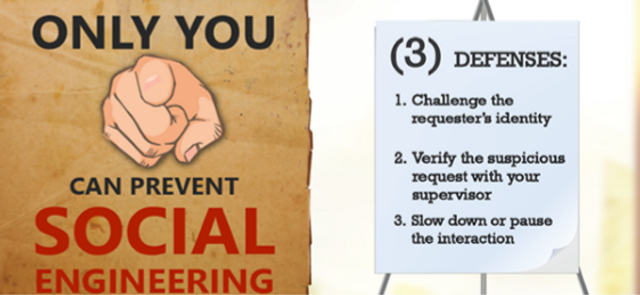
This brief video shows you how to recognize and prevent social engineering attacks.
1:31 minutes

This security awareness training covers privacy and EU General Data Protection Regulation for data processors.
11:08 minutes
This security awareness training covers Privacy and the General Data Protection Regulation for Executives.
14:53 minutes

This brief video covers the next steps for an organization should a breach occur.
1:43 minutes

This security awareness training covers Privacy and the General Data Protection Regulation for Executives.
14:37 minutes

A high level overview of the origin and aims of the General Data Protection Regulations
2:01 minutes

Please complete and submit the form below.

