HIPAA HITECH
Our role-based HIPAA/HITECH module defines Protected Health Information (PHI), explains the need for PHI security and outlines best practices for handling PHI.
14:16 minutes
*Courses may vary.
Search Courses

Our role-based HIPAA/HITECH module defines Protected Health Information (PHI), explains the need for PHI security and outlines best practices for handling PHI.
14:16 minutes
What can you do to prevent election fraud? More than you may think! In one short video, you’ll explore the dos and don’ts of ensuring a safe and secure election process.
3:55 minutes



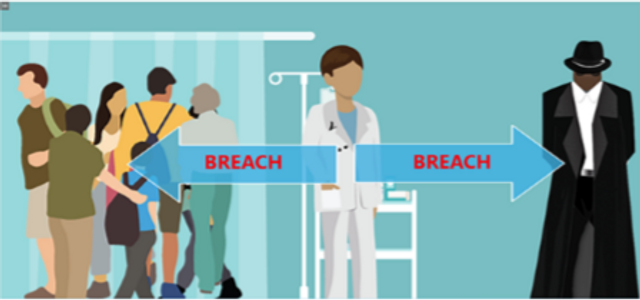
This module details HIPAA’s definition of a breach, breach disclosure requirements (including an overview of the concept of safe harbor) and recommended breach detection and notification methods.
8:54 minutes

This social engineering module teaches a three-step method to add clarity to a confusing conversation, verify suspicious requests and identity theft prevention prescribed by the Red Flags Rule.
7:21 minutes


This module explains the social engineering methods hackers use, review HIPAA requirements regarding external requests for PHI, and teach managers to work with staff to prevent PHI breaches and leaks.
8:49 minutes

Healthcare professionals are targeted by hackers via social engineering. This module will explain social engineering techniques in detail, and review HIPAA requirements regarding external requests for PHI.
9:33 minutes


This module will explain the various social engineering methods hackers use, and teach managers how to work with staff to prevent data breaches and leaks.
7:53 minutes

This module explains how to recognize advanced persistent threats (APT), APT risks and common attack methods.
7:22 minutes

Our Help Desk module explains how hackers can exploit the trust between a helpdesk and its users through social engineering attacks.
5:00 minutes
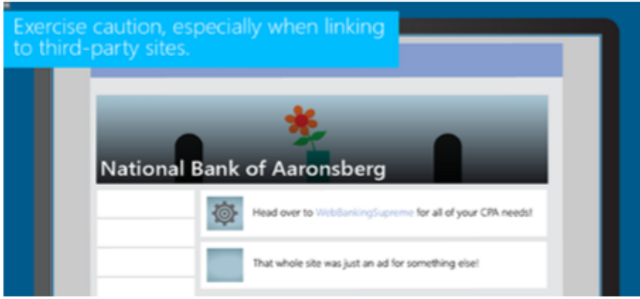
This module explains common security risks financial sector employees face when using social media at work, and ways that learners can protect themselves and their company from social media threats.
9:07 minutes

Introduces the concept of Identity Theft, common ways a person’s identity might be stolen, possible impact for an individual and an enterprise, and ways to protect your identity.
5:18 minutes


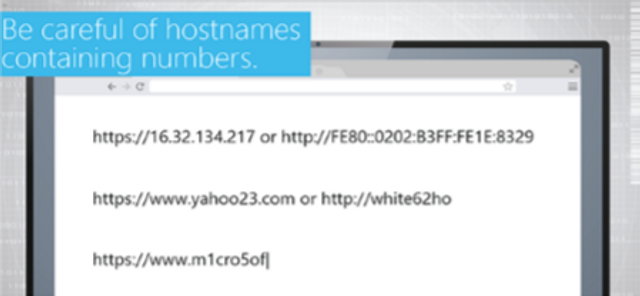
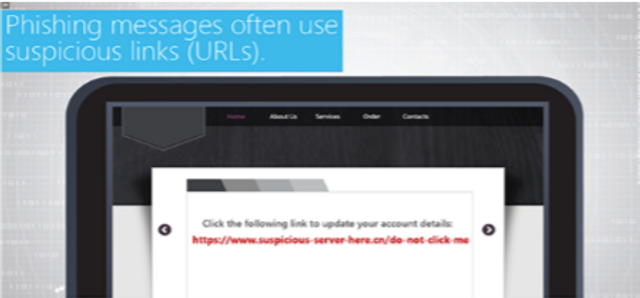
How to browse the web safely.
0:35 minutes
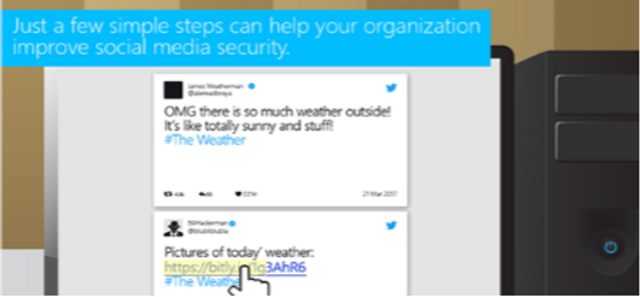
This module discusses the importance of data security and how to classify data.
1:29 minutes

Errors are a fact of life in any system. But what happens when an error report ends up revealing a weakness? Take a closer look at the problem of improper error handling.
3:26 minutes

Please complete and submit the form below.

